Ready for yet another post about predictions for 2019? Thank you for giving ours a chance as well 🙂
Implementing best practices for website security can be the difference between a successful website or a compromised one. A compromised site can have all sorts of nasty consequences that take time, money, and energy (aka grey hairs) to cleanup. Not to mention loss of revenue.
The major hurdle to implementing security is complexity. The more complex the security solution is, the less likely companies are going to adopt it. But, from our experience, many businesses can’t afford their site getting hacked, so it really is worth all the extra effort involved in preventive security measures.
With that in mind, let’s see what kind of website security trends are likely to take center stage in 2019.
1. MarSecOps
Short for Marketing Security Operations, the idea is that security is not just the realm of website developers or the IT department anymore, but rather the marketing department has an equal if not greater interest in, and even responsibility to security.
The rationale being that if your website gets compromised it is likely to result in loss of revenue, and generally the website falls heavily under the management of a company’s marketing team.
To look at it another way, website security is everyone’s responsibility since the success of the website affects everyone, especially the marketing team and the company’s bottom line.
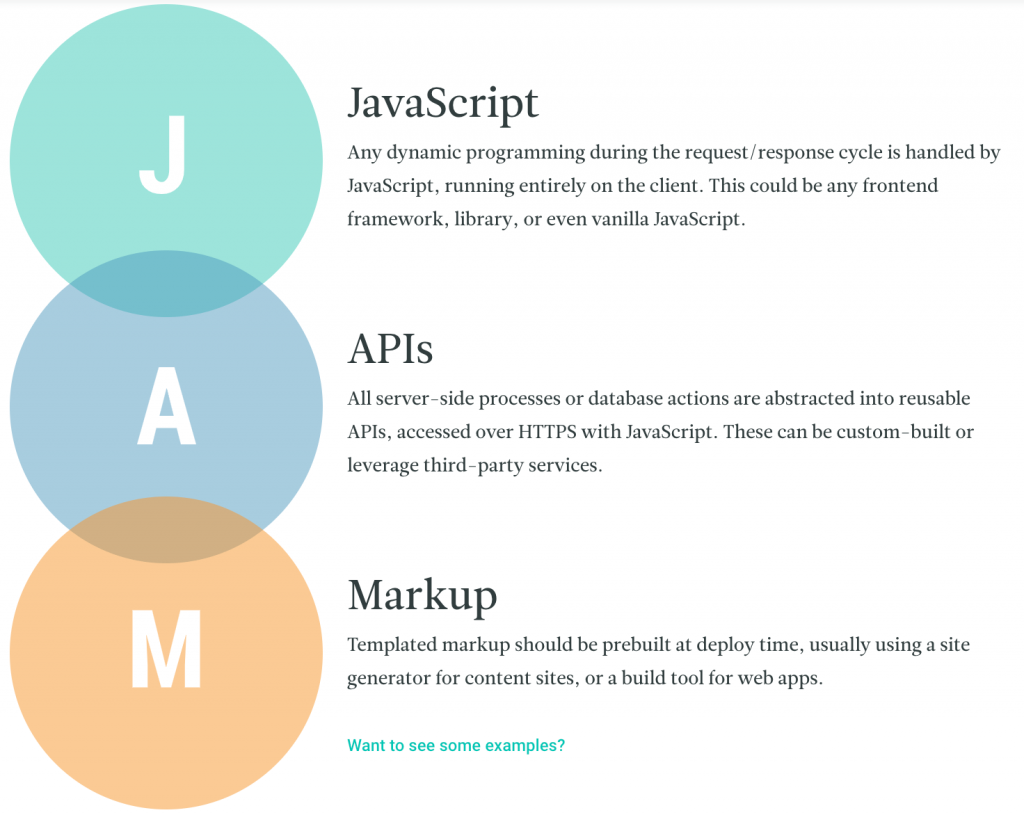
2. Static aka JAMstack sites
Databases are the target of attacks such as SQL injections and XSS (cross-site scripting) attacks, which are two of the most common types of attacks employed on websites running on Open Source software such as WordPress, Drupal, and Joomla.
Decoupling the front-end of a site from the backend and generating a static version of a website has major security benefits since it minimizes the attack surface and there is no longer a database to hack.
Static sites in this context are not referring to static sites of the early 2000’s but rather sites with robust functionality via Javascript, APIs and Markup, otherwise referred to as JAMstack.

3. HTTP Security headers (CSP and HSTS)
SSL is a necessary first step, but it’s not enough to fully secure your site.
Even if your site is SSL’ed and rocking a green padlock, there are still vulnerabilities that are commonly exploited and implementing HTTP security headers such as CSP and HSTS can help protect your site further.
Cryptojacking (using JavaScript on a web page to mine for cryptocurrencies) is a prime example of a rising threat that can be curtailed by security headers.

4. Fool-proof 2FA
Currently, 2FA (Two-factor authentication) is not the golden ticket to security, since there is still plenty of room for improvement. 2FA is typically a combination of a password and a code that’s sent to a user’s phone.
However, attackers can execute a SIM swap to gain access to a user’s phone, or they might find a leaked database with text messages open for snooping.
To combat this kind of attack, we shouldn’t depend on texting, emails or calls from the origin, but rather the codes should be generated by an application like Google’s Authenticator app. The recent Reddit hack was an example of 2FA gone wrong.
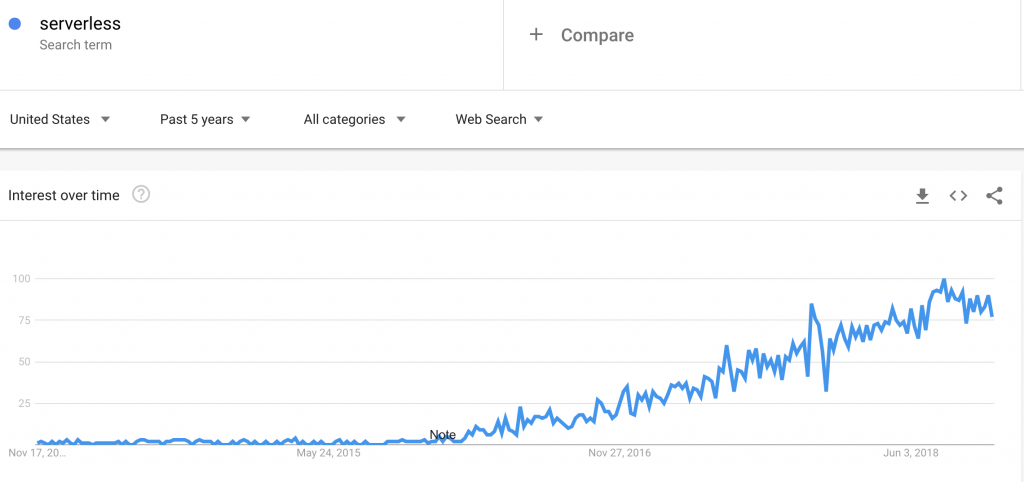
5. Serverless
Using serverless architecture instead of finite servers is gaining steady momentum.
With serverless, the infrastructure requirements are taken care of by the cloud provider, and updates take place automatically, so your systems are always up to date.
That means you don’t need to worry about outdated server software, one of the major ways that sites hosted on traditional LAMP-based servers can get hacked.
In conclusion
The only way to be 100% certain that your website won’t get hacked is… to not have a website.
If a hacker is bent on hacking your site, they probably will.
But, the majority of hackers are trying to find the easiest route to hack into a site and try to take advantage of weak or stolen passwords, or vulnerabilities due to outdated software.
So what’s the best way to secure your site?
First, make sure you’ve covered all the low-hanging fruit such as using strong passwords, having proper backups, and limiting login attempts.
Second, if you want to ramp up your security even more this coming year, then consider learning more about the above-mentioned security measures.



